Role Based Access Control
Introduction
RBAC (Role-Based Access Control) is a security model that restricts access to system resources based on the roles assigned to users within a Gemini Detect instance. In this implementation, users are assigned to one or more groups, which are then granted access to specific Detect resources based on their subset of roles. Gemini Detect RBAC is highly flexible and allows for the creation of custom roles and groups to meet the needs of any organization. In most use cases, the default roles and groups will be sufficient and are recommended for use.
Admin Console
The Admin Console is a web-based interface for managing the RBAC system. It is accessible by clicking the gear icon beside your username in the bottom right corner of the the Gemini Detect Viewer. This will open a new tab in your browser. Only System Admins and User Admins have access to the Admin Console.
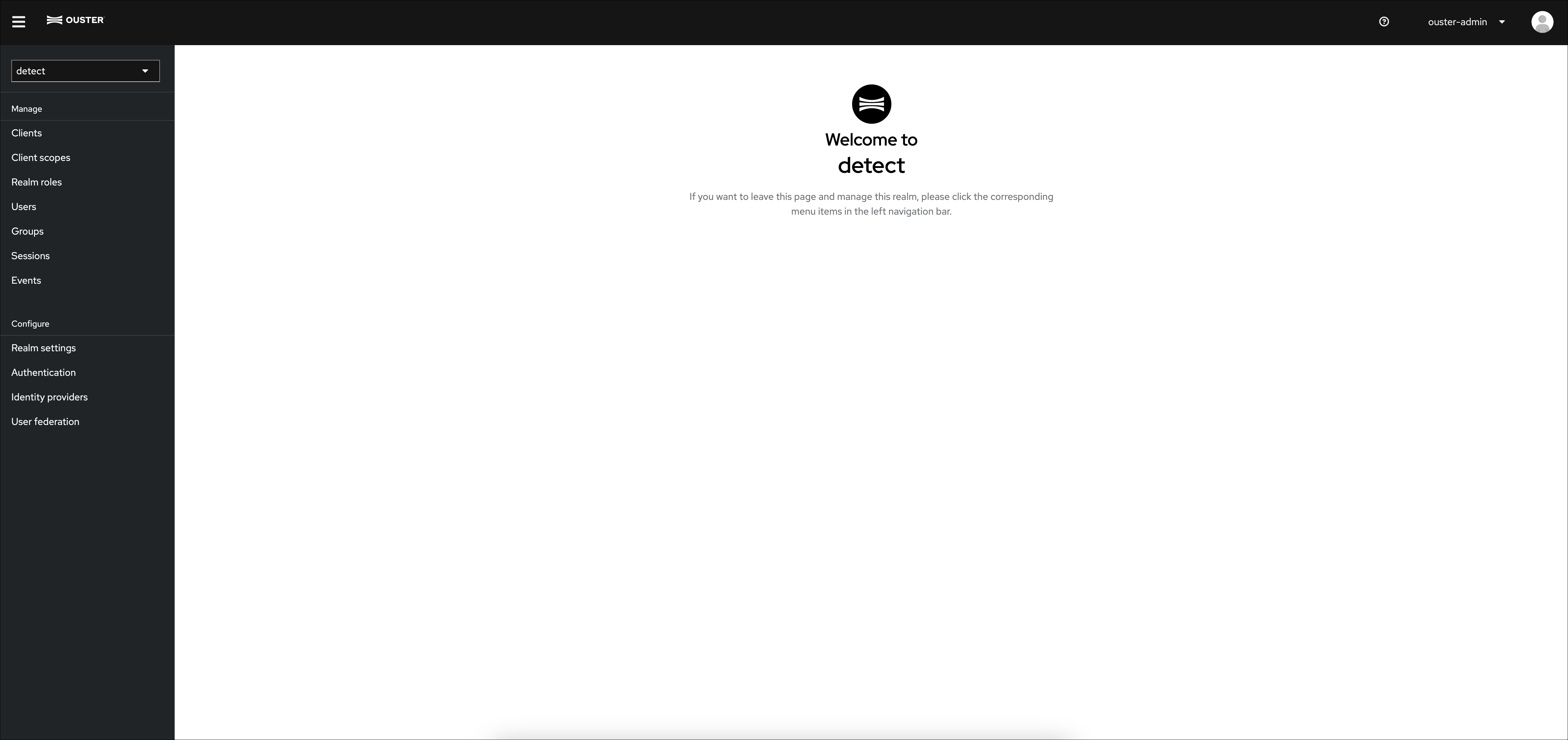
Admin Console
Account Console
The Account Console is a web-based interface for managing your Gemini Detect account. It is accessible by clicking the gear icon beside your username in the bottom right corner of the the Gemini Detect Viewer. This will open a new tab in your browser. Detect Admins and Detect Viewers only have access to the Account Console.
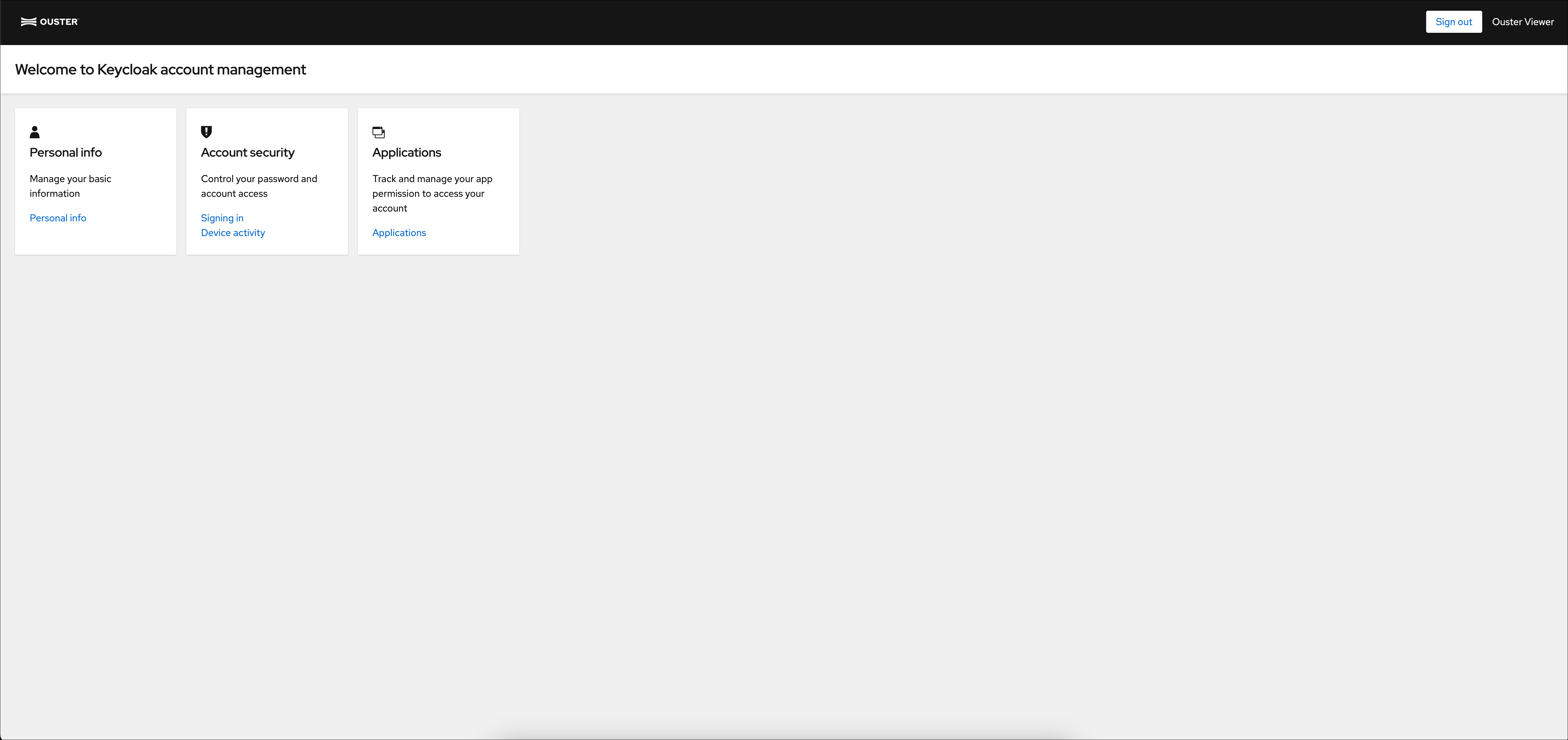
Account Console
Default User
A default user is created when a Gemini Detect instance is first initialized. This user is assigned to the System Admin group and is used to manage the RBAC system. The default username is ouster and the default password is Stone-Pass-Fill. On first login, the user will be prompted to change their password. This password is subject to a default password policy, which requires a minimum of 13 characters, 1 special character and 1 uppercase character. This password policy can be modified in the Authentication section of the RBAC Admin Console.
Note
The default user can be deleted, but it is important to create another System Admin user before doing so. If the default user is deleted without creating another System Admin user, the RBAC system will be inaccessible. Contact Ouster support for assistance if this occurs.
Default Groups
A set of groups is used to manage the two main components of a Gemini Detect instance: the Detect services and the RBAC system. The Detect services are the various API endpoints that are used to interact with the Gemini Detect (e.g., adding sensors, modifying zones, etc.). The RBAC system is the set of APIs that are used to manage the RBAC (e.g., creating users, assigning roles, etc.).
Detect Admin: This group is used to manage the Detect services. Users in this group will have access to all Detect services.
Detect Viewer: This group is used to view the Detect services. Users in this group will have view access to all Detect services, with the exception of perception settings and networking.
System Admin: This group is used to manage the RBAC system. Users in this group will be able to manage the RBAC system as well as all Detect services.
User Admin: This group is used to manage users. Users in this group will be able to manage RBAC users as well as all Detect services.
User Management
Users can be managed in the Users section of the RBAC Admin Console. Users can be created, modified, and deleted. Users can also be assigned to various groups and roles. The System Admin or User Admin group is required to manage users. Select Add User to create a new user.
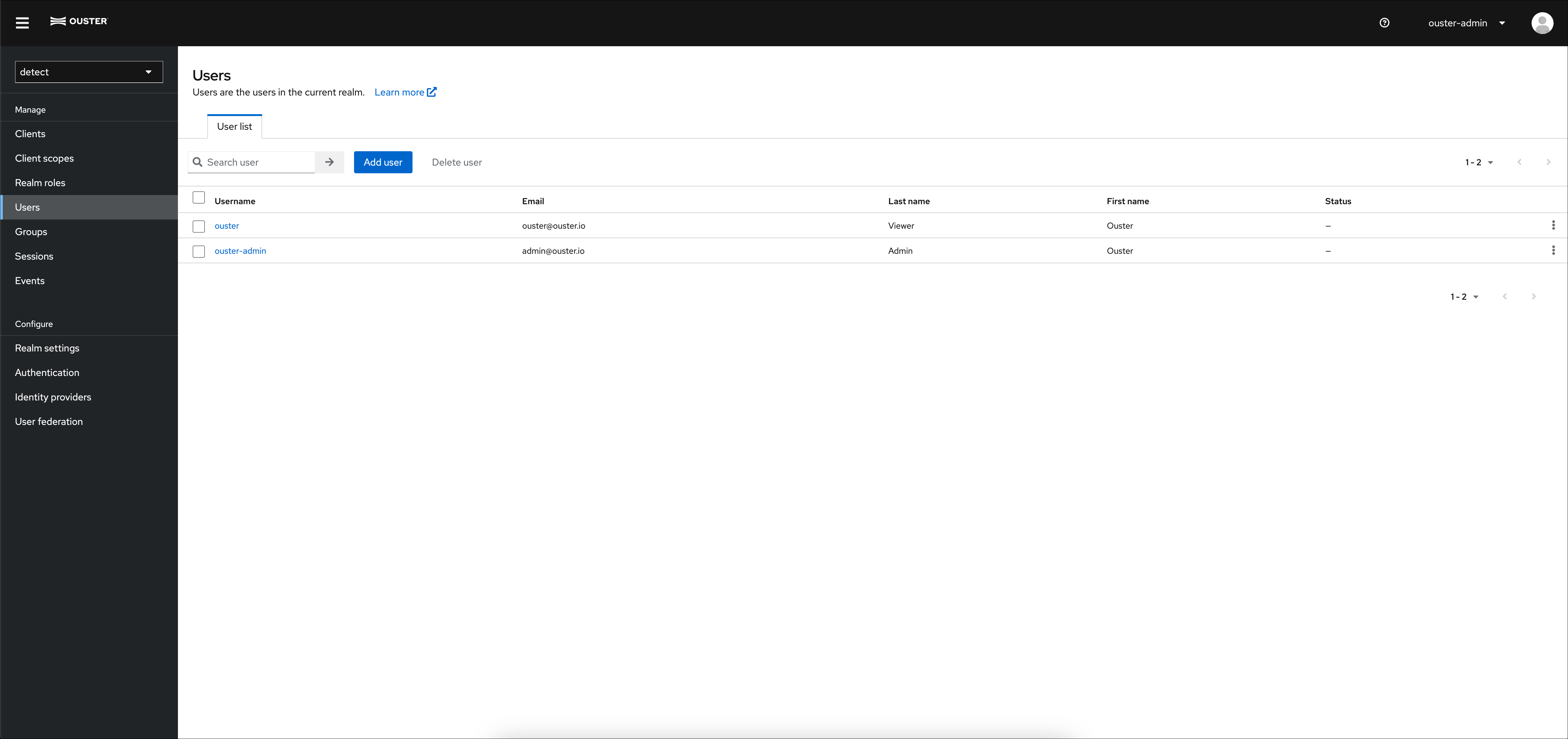
User Management
During user creation select Join Groups to assign the user to one or more groups. User groups can be modified at any time in the Groups tab of a user.
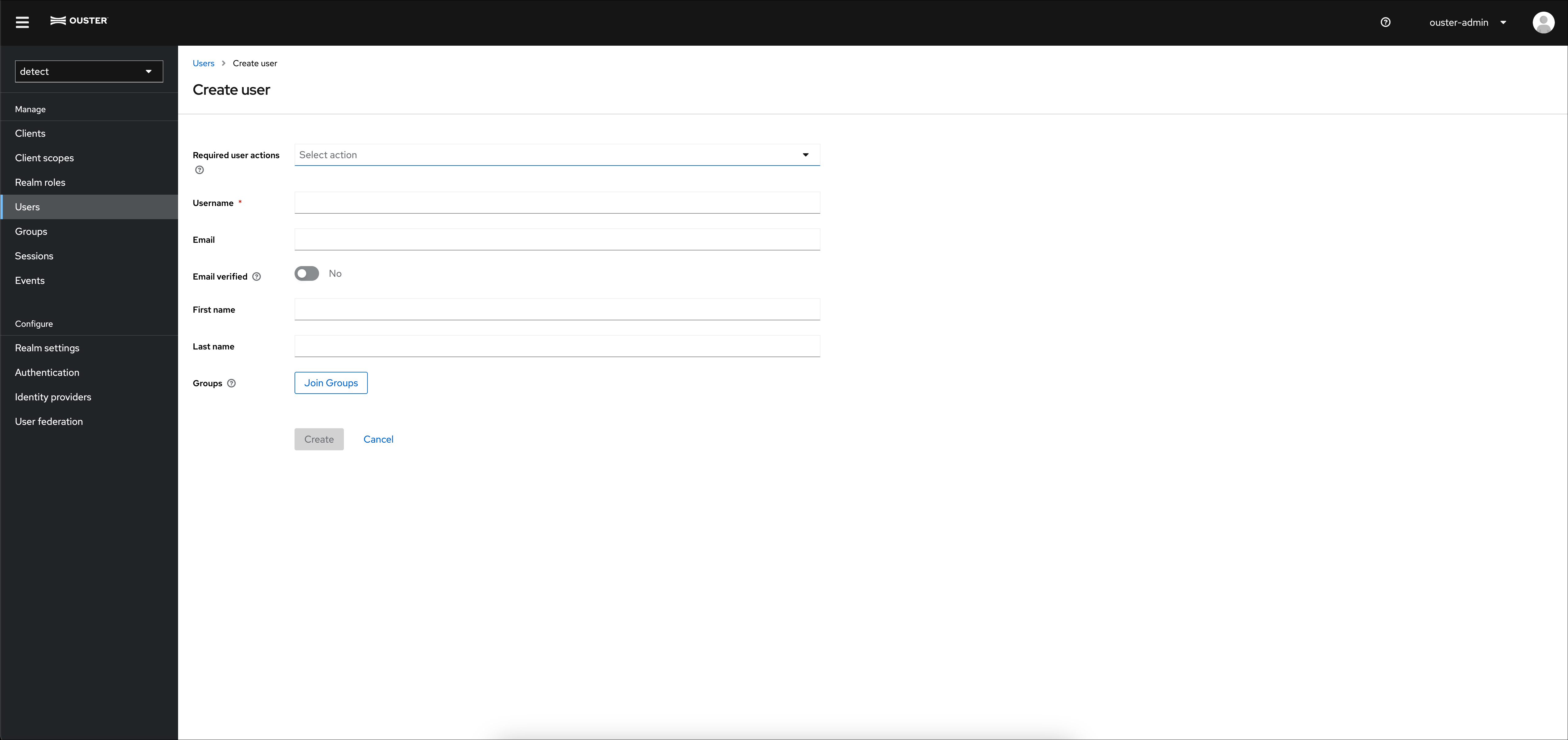
User Creation
Once a user is created, they need credentials to log in. Click on the new username, go to the ‘Credentials’ tab, and click ‘Set Password.’ It’s recommended to set a temporary password, which will prompt the user to change it on their first login.
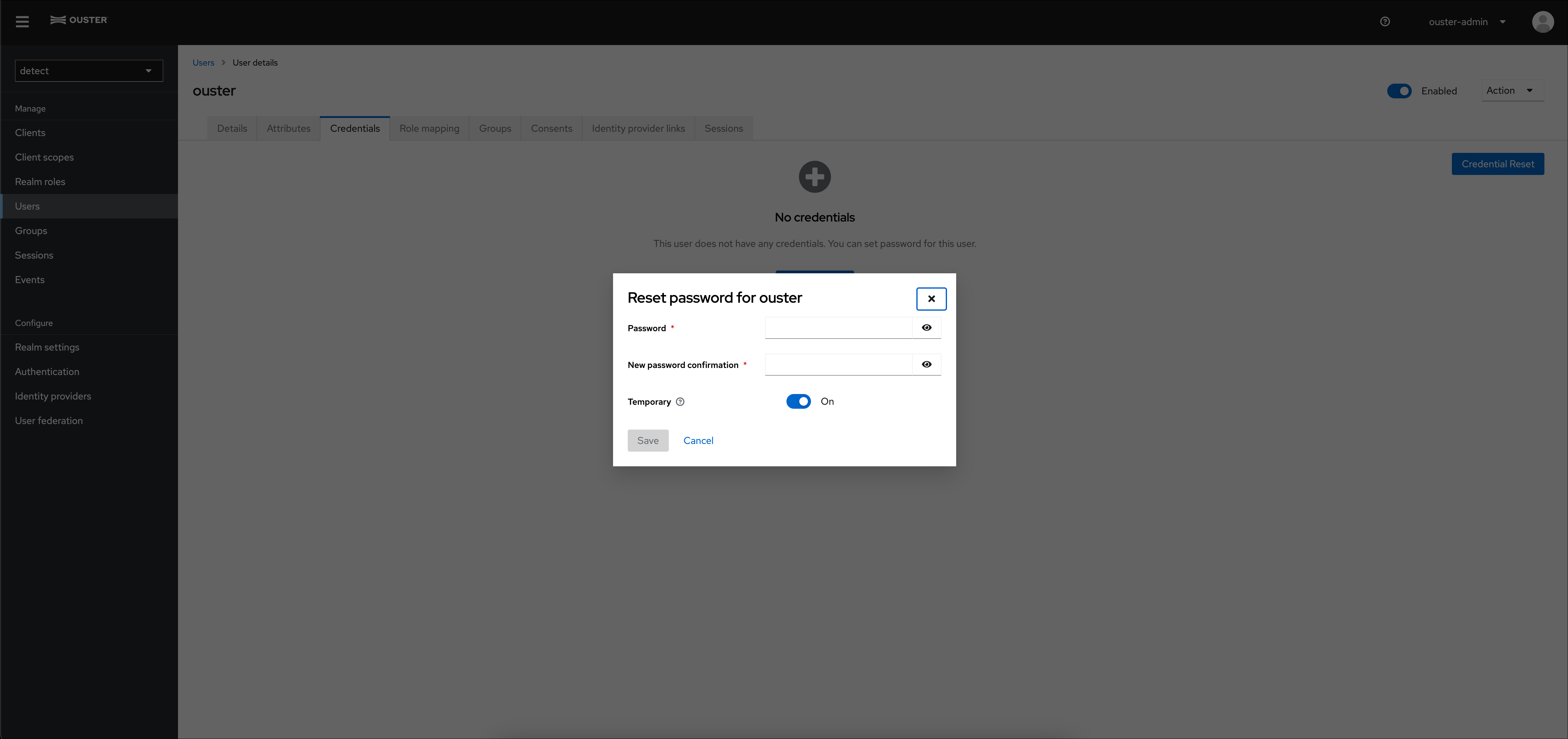
User Credentials
Forgot Password
When a user forgets their password, they will have to contact the
System Admin or User Admin to initiate the password reset process. A
System Admin can navigate to
Users -> <username> -> Credentials -> Reset Password to
initiate the password reset process.
Admin Forgot Password
If a system admin forgets their password, a script exists on the system to reset the password. In a terminal window on the Ouster Gemini Detect server, run the following command:
sudo /usr/bin/reset_user_password.sh ouster <new_password>
Advanced Configuration
Gemini Detect RBAC is built on Keycloak Authorization Services, offering a powerful and flexible system that supports a wide range of use cases. While configuring many of these use cases is beyond the scope of this document, the Keycloak documentation serves as a valuable resource for advanced configurations. Below are examples of some advanced configuration options.
IDP (Identity Provider) Initiated Login
LDAP User Federation
SAML User Federation
OpenID Connect User Federation
Group and Role Customization
Admin and User Audit Logging
Developer Access
Users creating applications to interface with Gemini Detect service APIs will need to implement client-credentials OAuth2 flow. This flow is used to authenticate the application (as opposed to a user) when the application requests access to Detect APIs. When implementing this flow, the application will need to provide the client-id and client-secret. The client-secret can be obtained in the Clients section of the RBAC Admin Console. The client-id is always detect-client, select the detect-client and click the Credentials tab to view the client-secret.
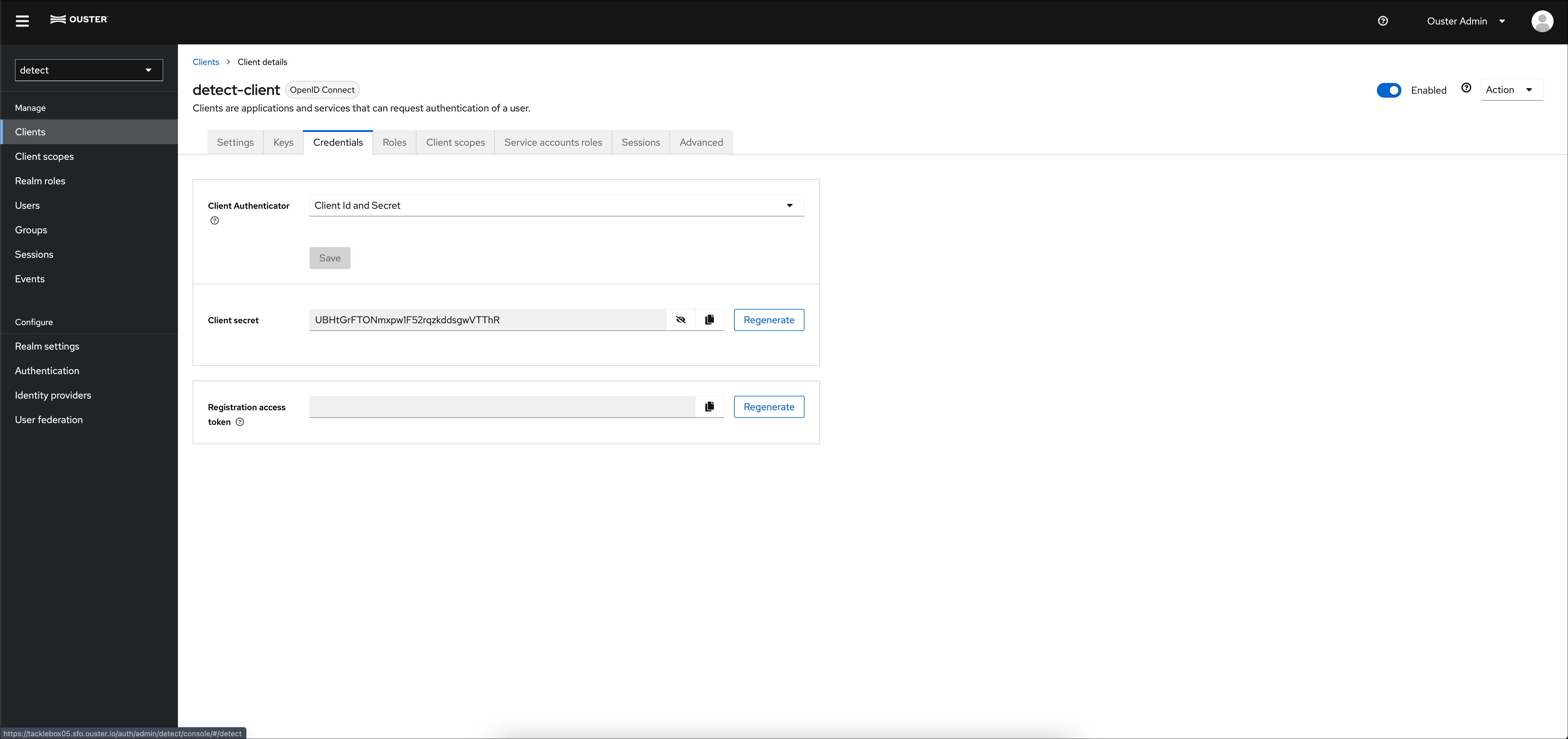
Client Secret