Accessing Gemini Detect Software
Ouster Registry
Gemini Detect artifacts can be found in the Ouster Registry. This repository requires an invitation to access. Please contact your Ouster representative if you have not already been provided an invitation.
Identity Token
An identity token is a long string consisting of alphanumeric characters. These tokens are scoped and revocable, making them more secure than using a password for software registry access.
In addition, their lack of special characters makes them easier to parse programmatically. To facilitate software installation and updating, the user must create an Identity Token in the registry. This token is used in place of your password for performing software installation and update tasks.
Creating an Identity Token
After purchasing the software, the customer will receive an email similar to the one presented in the screenshot.
The user must click Accept invitation to begin the software registry account creation process.
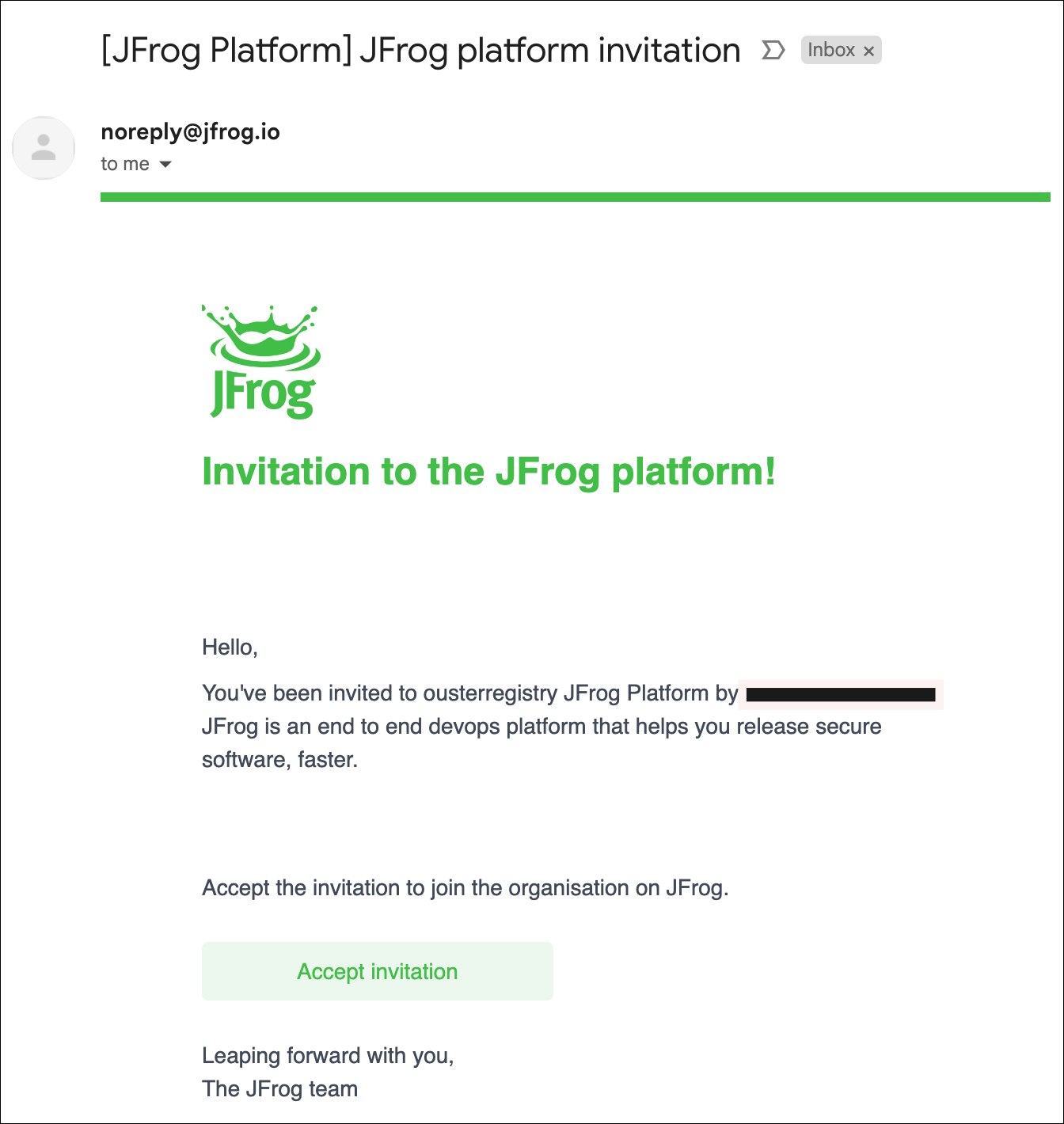
JFrog Platform Invitation
The user is then brought to the account creation web page.
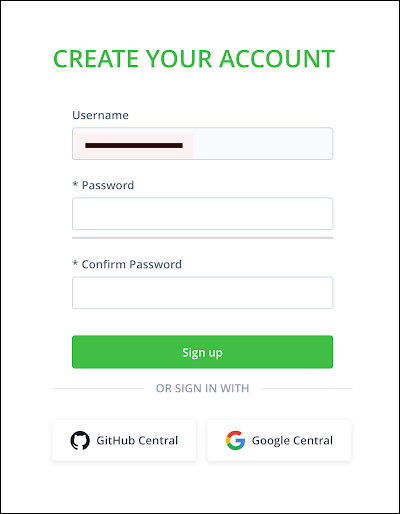
JFrog Create Account
A new password for the account must be supplied or, alternatively, the user may choose to sign with through sign-in partners GitHub or Google.
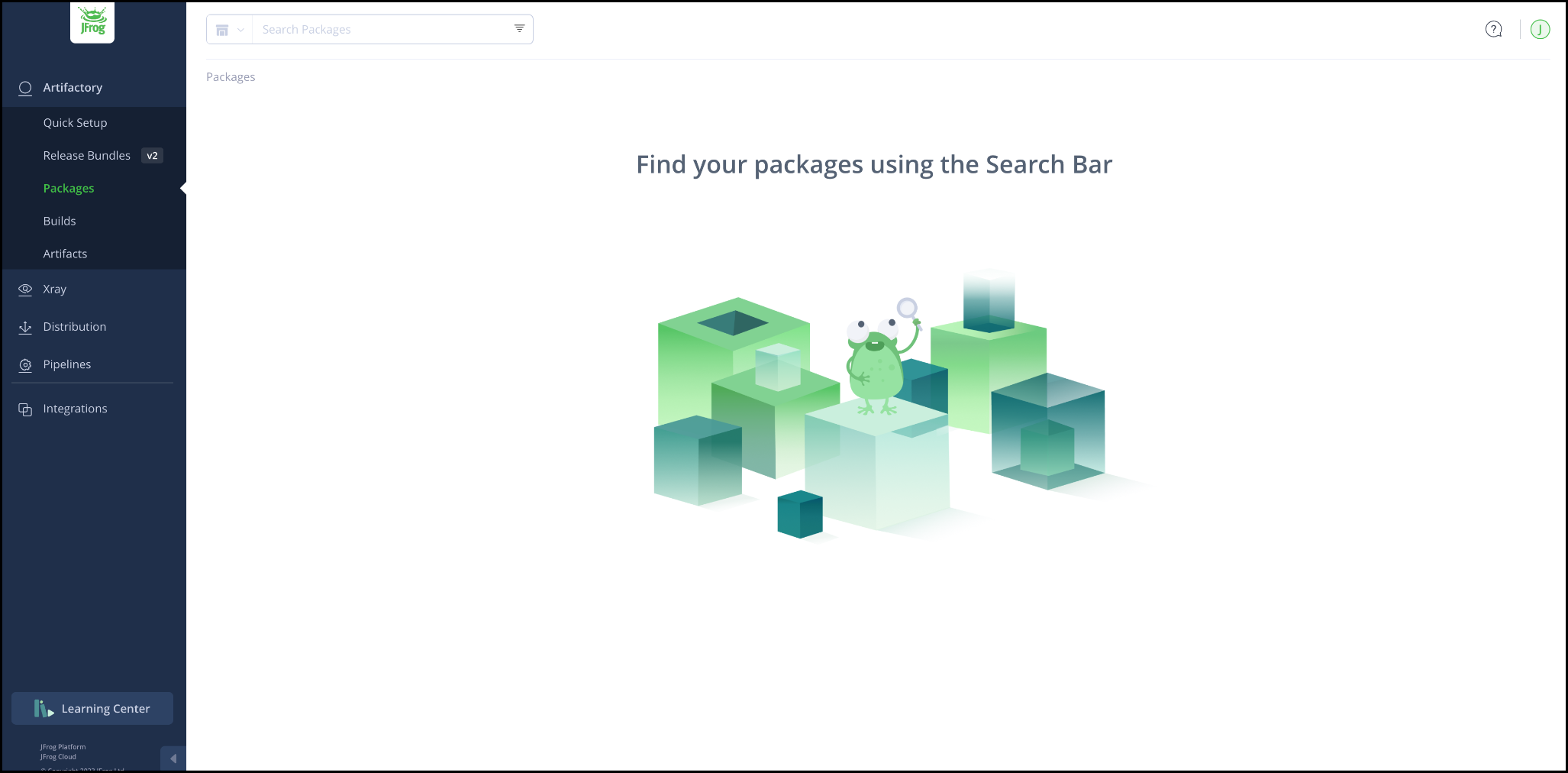
JFrog Dashboard
Note
The above image is the initial screen presented after successfully creating account.
Click user account on the right top corner and select
edit profile.
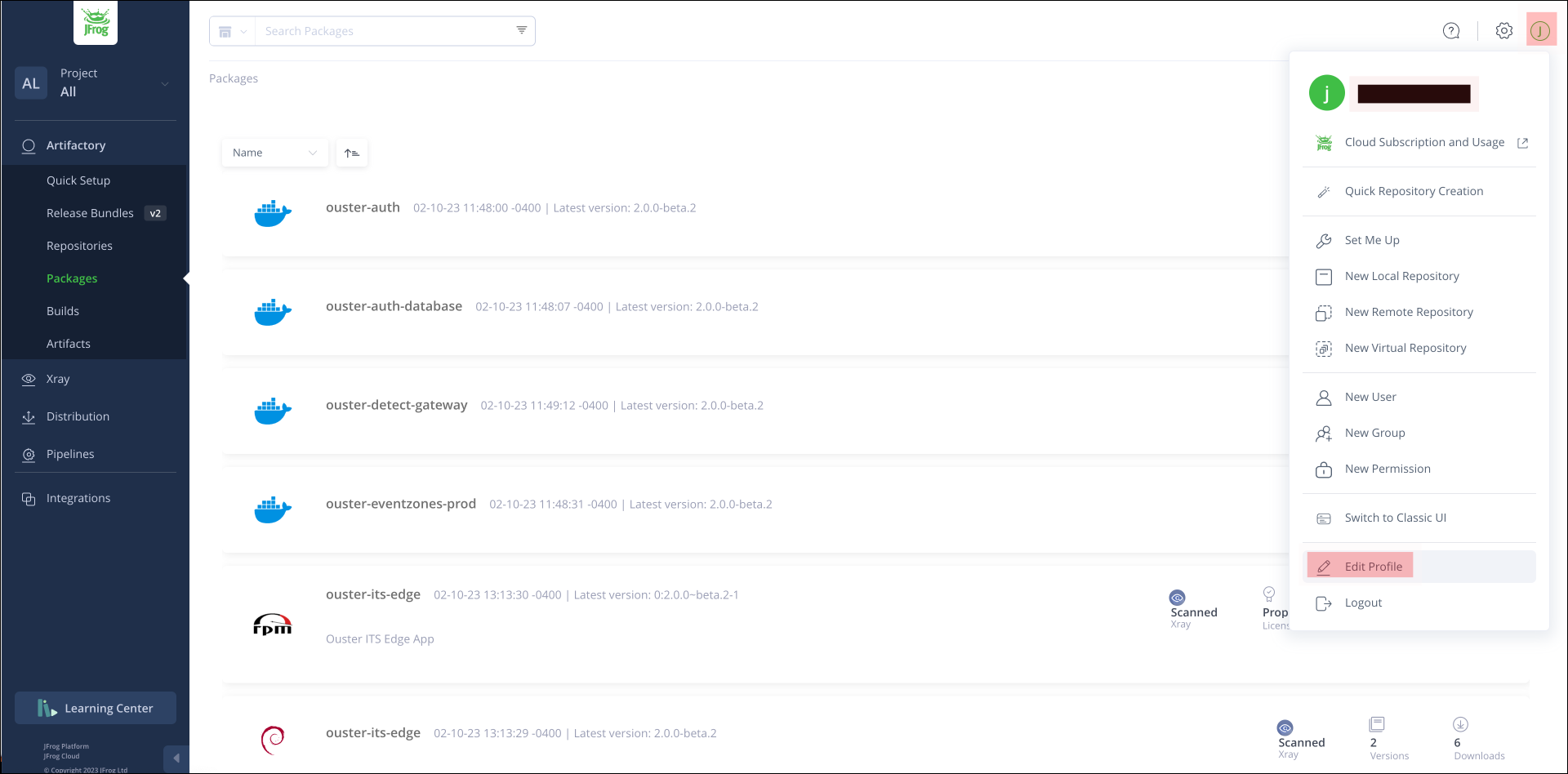
Edit Profile
Enter password, and click unlock.
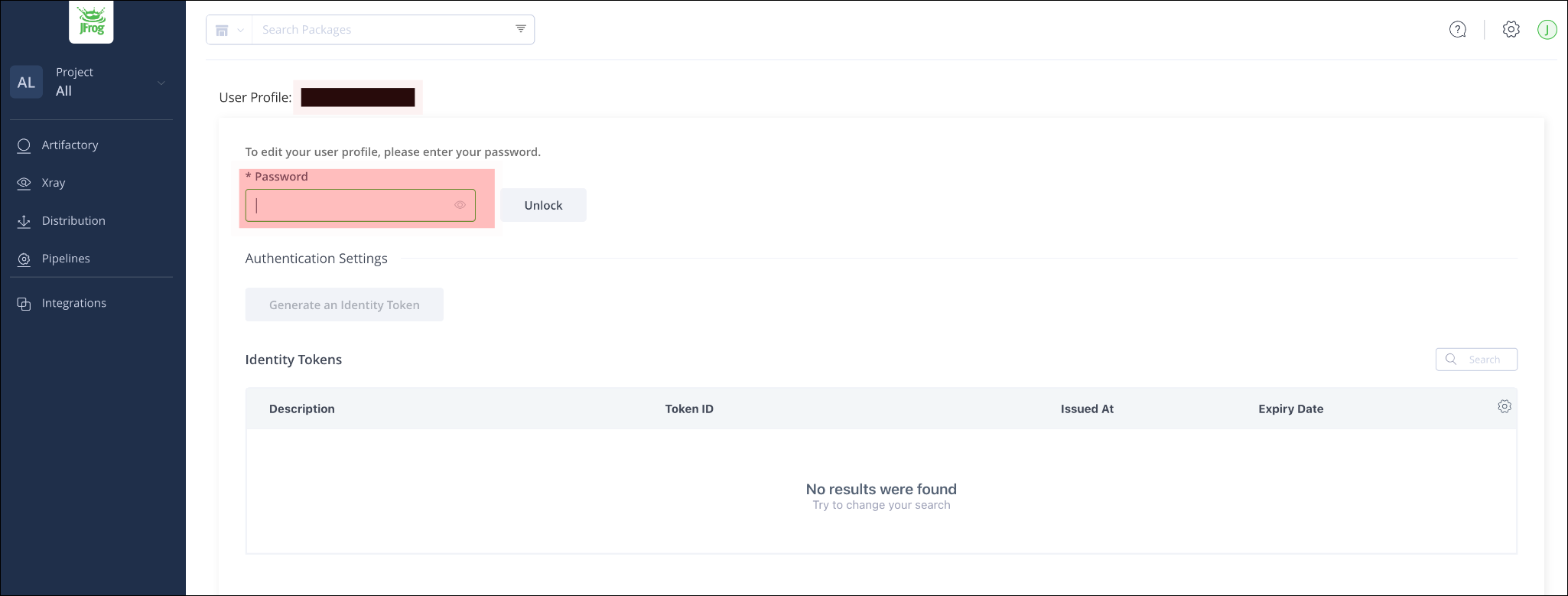
Unlock profile
Click on
Generate an Identity Tokenand add a description if required, clickNext.
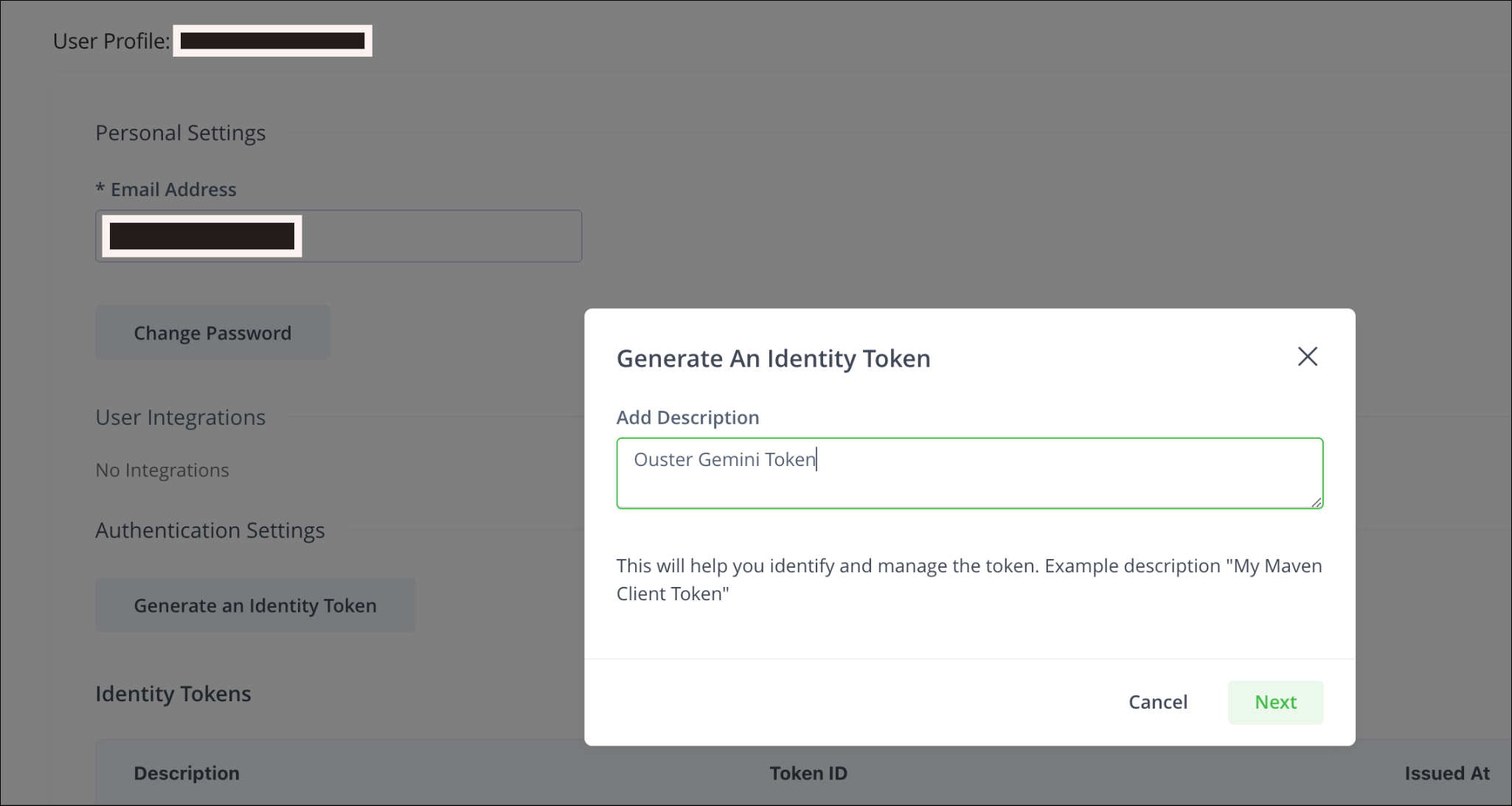
Generate Token
Note
The user must store the token in a safe location, such as in a password manager. Once this dialog box is closed, it will no longer be possible to retrieve the token. When retrieving software from the registry, this token should be used in place of the user’s password.
This completes the token generation process.
Tar Archive Download
For offline installations or performing updates through the Detect Viewer, you can download the Gemini Detect tar archive from the Ouster Registry. Once logged into the Ouster Registry, select the Artifacts on the left-hand side and expand gemini-package-stable -> detect in the tree. Within the detect folder, select the desired version you want to update to. Once the version is expanded, find the archive based on your platform (e.g., select detect-amd64-2.0.0.tar for version 2.0.0 for x86_64 edge devices). If you’re updating an edge device using Detect Deep Learning, select the archive with vella in the name (e.g., detect-vella-amd64-2.0.0.tar).
Right-click on the archive and select Download.
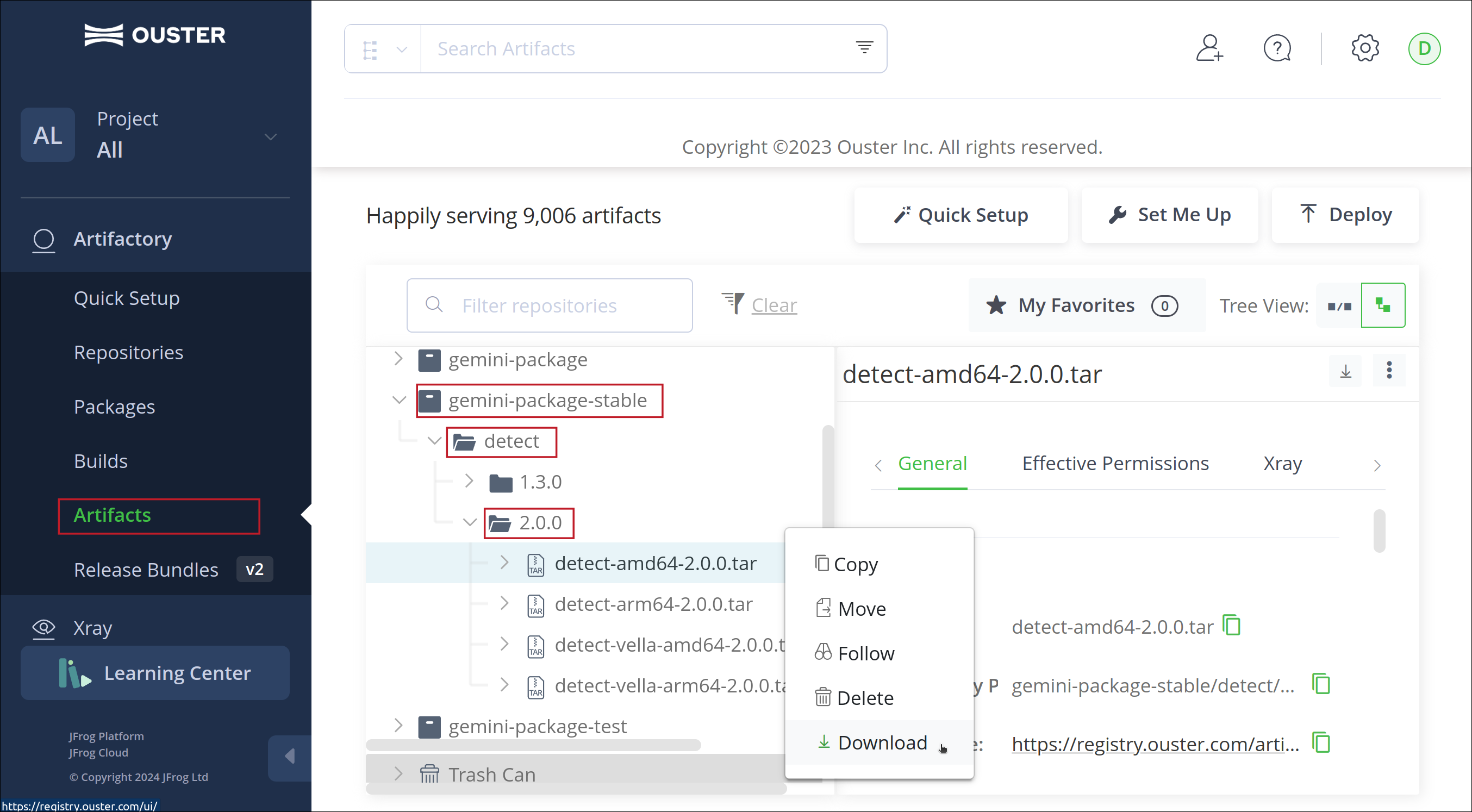
Tar Archive Download